Process Mining Feasibility Study Report for We-Deliver
Instructions:-
Process mining (PM) is a young technical field that arises only around a decade ago. Its powerful capabilities to enable an organisation to understand, monitor, (re-)design and improve its processes and operations, however, have caused much attention. PM is with great potential for further development and deployment.
In this coursework, you are asked to create a consultancy feasibility study report in PM for a transportation company, We-Deliver.
We-Deliver is an international company that owns over 100 trucks covering over 500 different delivering destinations in Europe. It runs a complex operation that oversees 20 offices and 60 warehouses in Europe. Its core business is to deliver goods for its clients. However, its operations are hindered by (unexpected) problems, e.g. late/frequent changes of (assigned) drivers, frequent change of delivery routes and destinations, delayed delivery (e.g. due to the fact that stocks to be delivered not available for loading), dropped/delayed/altered of delivery plan (i.e. which order to deliver and whether an order will be fulfil in multiple deliveries), goods transported not been off-loaded correctly due to confusion, overflowing of warehouses that goods need to be re-routed to be stored in different places, back log of delivery and therefore further delays, change of customer orders (caused by their clients – external factors), etc.
Due to all of these problems, the company is losing profit and customers. The company therefore wishes to understand where it went wrong in its operations and how it may improve them. It also wants to investigate what may be the ultimate operation model, e.g. to determine best delivery plan for its orders, what customers should be prioritised, what types of orders are most profitable, costly, complex or easy to do and how its operations may be streamlined to support all of that.
You are asked to create a consultancy feasibility report to investigate whether process mining (PM) would be a suitable technology for this company. However, the company does not know what PM is. You therefore need to firstly educate the company about PM, followed by a recommendation of how PM may be used for the company. You also need support your arguments by explaining its usefulness using company specific examples, e.g. solutions to shed lights in the above discussed problems. To help the company understand what will be required of them in a PM project, you should explain the activities involved in a PM project.
In this report, focus on the functionalities of the tool only, you are not required to assess the cost/financial aspects of the tool. You are encouraged to provide graphs and comparison tables to help your explanation, where appropriate.
Part I – An Overview of Process Mining (50% for UG) (45% for MSc) – 1-2 pages
Explain what process mining is and what types of functionalities that it offers. Explain in general terms, the overall concepts of PM, what resources (e.g. software systems and models) and activities are involved; and where PM may be useful for an organisation. Use graphs to help your explanation.
Part II- Investigating Process Mining for the company (50% for UG) (45% for MSc) – 1-2 pages
In this section, you offer specific analysis and recommendations to the company, based on their operational and organisational context. You should talk about why PM is useful for the company and in what aspects. You should also talk about what resources will be required by the company. To do this part, you should contextualise the points that you have illustrated in part I and discuss them in the company’s context.
Part III – Investigating and recommending possible software for the company (10% for MSc) 1-2 pages
Investigate the commercial PM software, Celonis, as kindly offered by Celonis.com, as a part of the course; and determine how Celonis as a PM tool may be useful for the company. You should compare the proposed useful functions for the company in part II and functions offered by the Celonis system, and explain how the company may use Celonis to help their operations.
In this report, focus on the functionalities of the tool only, you are not required to assess the cost/financial aspects of the tool. You are encouraged to provide graphs and comparison tables to help your explanation. In particular, a comparison table will boost your mark.
Overall Marking Scheme and Instructions:
Report length:
The report length above is provided as a guideline for suitable length. You do not need to stick to it strictly, if you need less or more pages. The most important point is to provide a good quality report with good content. Lengthy report may not earn extra points. Similarly, shorter report may not lose points either, if it is concise, insightful and to the point.
References and citations:
If you are not sure what We-Deliver’s business model, rules or mission are, you can consult relevant web sites of transportation companies for information and should cite relevant URLs (web site addresses) in your report. If there are details that are still unclear, you should make your own assumptions and create your report based on your assumptions. However, if so, you must make clear whatever assumptions that you have made in your report. You are welcome to add additional references of your own. Providing relevant citations in addition to the ones already provided here to support your arguments will boost your marks. References using good style citation are worth of 1 mark, as embedded in the above marking scheme [3].
Other important characteristics:
Good structure, high readability, good logical flow of arguments, no spelling errors, self-written, high originality, good insights, and proper citations if any.
All of the good practices listed in the marking criteria will count, as together they support the good quality of your paper. As an estimate, the structure and syntax based factors will probably occupy something between 5-10% for each of the questions above. For instance, a poorly spelled, ill-structured, logically not following/understandable (e.g. claims not supported by reasoning and references) and poorly cited paper will greatly decrease the readability and credibility of the paper.
For the rest of the report, it would probably be evaluated based on the criteria of self-written, originalities, insightfulness, and personal understanding and judgements of the topics, etc.
Deadline and Submission Method:
Deadline: 3pm, March 31, 2016 (Please note that standard departmental late penalties is applicable. Currently the penalty is 10% per working day late. Note to allow late and multiple submissions, the Vision submission deadline will be set at April 7th, which is not the real deadline. )
Submission method: submission via TurnItIn, Vision only. You should submit only one file and it should be named as:
Firstname.lastname.doc; or
Firstname.lastname.pdf.
You can submit your file several times. New submissions will overwrite previous submissions. The last try of (re-)submission will be April 7th, penalties applicable though.
Key words:
- Contract logistics
- 3rd party logistics
References:
- IEEE CIS Task Force on Process Mining, Process Mining Manifesto, 2011: http://www.win.tue.nl/ieeetfpm/doku.php?id=shared:process_mining_manifesto
- Jon Espen Ingvaldsen and Jon Atle Gulla, Model-Based Business Process Mining: https://scholar.google.com/citations?user=lq5InSEAAAAJ&hl=en
- How to provide references: http://www.macs.hw.ac.uk/~yjc32/project/student-notes/writing-advice/how-to-provide-references/
- Supply Chain Logistic companies: https://www.wikijob.co.uk/content/industry/transport-logistics/list-transport-logistics-supply-chain-firms
- Ceva, example logistics company: http://www.cevalogistics.com/contract-logistics
Solution
Process Mining Feasibility Study Report for We-Deliver
Introduction
As businesses grow, information process increase in number making them more complex and hard to maintain. Information processing is key to the performance and coordination of services in any company or organization. Process mining technologies have over the past few years proved to be providing managers with an understanding on how to analyze information and create realizable control flow perspectives in a business environment. In business context, process mining is defined as part of business intelligence that allows business processes to be analyzed based logs of events. During the analysis, a data mining algorithm is designed and applied to data events identifying trends and patterns that are available in the data. it is also referred to as an automated business process.
Process Modelling and Analysis
Most of the contemporary business management trends like business activity monitoring management or business operations and process intelligence apply functionality using technology. As such, workflow management systems are continuously being integrated in the business environment. Figure 1 represents a basic process mining process and implementation. From the diagram a special classification of events and data based on occurrence distinguishes the techniques that are used to arrange the events into logs. According to Ailenei (2011), process mining occurs in three steps; discovery, conformance, and enhancement. At the discovery stage, a process model is defined, discovered and visualized. During conformance, a comparison is made between the pre-defined ideal process and the real or actual process. At the enhancement stage, additional information is added to the discovered and existing models. The information usually adds value to the models based on performance trends, costs, likely occurrences and probabilities, and social structures.
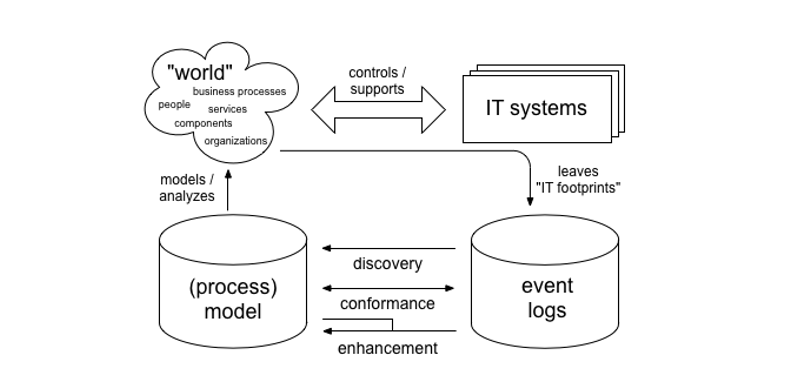
Figure 1: Illustration of a process mining
The basic idea behind process mining is the extraction of knowledge based definitions from events and logs stored in an information system. As a result, the solution provided is an improvement of the actual process and based on the factual and real information that has been collected when the processes were being executed. Over years, process management for informatics in sectors where independent processes converge to form complex models has been a constant problem (van der Aalst & Weijters, n.d.). Under such circumstances, not only will the managers be unable to understand the process but also domain experts. This makes it impossible to make a reality out of a process model. But with the advent of technology in business environments, data can be captured in a system and a process mining tool used to create event logs depending on the sequence of occurrence on the data.
After creating the event logs, an automatic reconstruction of the event is designed as a model explaining the behavior of the event as observed over some time. For instance, one can define and construct a process and remodel it with a new set of characteristics based on its complexity or rate of appearance. The application techniques commonly used in process mining are data mining. Big data is obtained from performance and occurrence recorded data and analyzed to generate a business process. In this case, instead of analyzing data from the explicit designs, process mining initiates the extraction knowledge process to extract key information from the execution logs (Ailenei, 2011). This is done using based on the alpha algorithm which typically assumes that each event corresponds to a well-defined activity and every event represents a case or process instance.
Application of process mining at We-Deliver
As stated in the case description, We-Deliver, a transport logistics company with one hundred trucks, 20 offices and 60 warehouses across Europe is faced with a challenge managing its processes and operations. Due to the lack of proper monitoring process, the company is experiencing high driver turnovers, changes in the routes and destination, delayed deliveries, warehouse overflow, changes in customer orders, and offloading problems. This uncoordinated processes have made the company fail to realize profits and is now incurring losses. Introducing process mining in the fleet and process management system can help the company contain its operations and realize good profit margins. Even though process mining has its scientific and practical challenges, understanding the discoverable processes and the amount or type of data required to provide adequate information will help the company to come up with a stable domain.
In the case of We-Deliver, the process mining will start by gathering data and information on the processes and events as they take place. Currently, the order of events at the company is not reliable and the system has failed. As a result, it shall be assumed that the events taking place from now onwards are the only reliable leads that can help define the business case and events form the logs. This shall make it possible to record new events and have reliable information about the events and the order in which the events occur. There are transactional systems which have to be embedded in the process mining to make it capture as much information as possible. Enterprise resource planning, business-to-business, customer relationship management, and work flow management are some of the important systems that will enable data capture in a reliable way (van der Aalst & Weijters, n.d.). An assumption can be made implying that collecting a process log and the order in which the events occur is not a challenge. The collected process log will be used to in the construction of a process specification. The process specification is always used to model the behavior of the registered event.
To illustrate further, We-Deliver is a huge company with so many processes. For this case, five cases can be used to execute four tasks. Assuming case A represents the truck, B for driver, C for goods under transit, D for customer, and E for loading personnel, then the corresponding tasks can be defined as task A for transportation, B for loading, C for offloading, and D for making an order (Ailenei, 2011). Since a case may be involved in multiple tasks, room shall be left for additional tasks for the same case. The log in table 1 shows how process can be evaluated.
Table 1: sample process log.
| Case identifier | Event identifier | Time stamp | Task identifier |
| Case 1 | 001 | 08.00 hrs | Task A |
| Case 2 | 002 | 09.00 hrs | Task A |
| Case 3 | 003 | 07.30 hrs | Task A |
| Case 3 | 004 | 08.30 hrs | Task B |
| Case 1 | 005 | 13.00 hrs | Task B |
| Case 1 | 006 | 13.00 hrs | Task C |
| Case 2 | 007 | 13.30 hrs | Task C |
| Case 4 | 008 | 11.00 hrs | Task A |
| Case 2 | 009 | 11.30 hrs | Task B |
| Case 2 | 010 | 12.50 hrs | Task D |
| Case 5 | 011 | 07.30 hrs | Task E |
| Case 4 | 012 | 16.00 hrs | Task C |
| Case 1 | 013 | 18.00 hrs | Task D |
| Case 3 | 014 | 12.00 hrs | Task C |
| Case 3 | 015 | 12.00 hrs | Task D |
| Case 4 | 016 | 10.00 hrs | Task B |
| Case 5 | 017 | 09.00 hrs | Task F |
| Case 4 | 018 | 13.40 hrs | Task D |
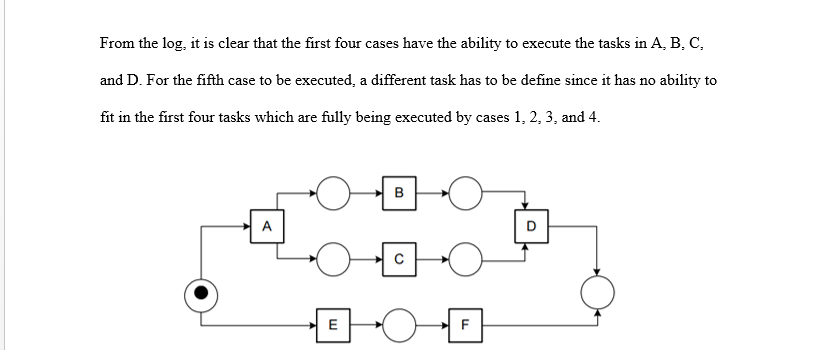
From the log, it is clear that the first four cases have the ability to execute the tasks in A, B, C, and D. For the fifth case to be executed, a different task has to be define since it has no ability to fit in the first four tasks which are fully being executed by cases 1, 2, 3, and 4.
Figure 2: process model for the log
According to Van der Aalst & Weijters (n.d.), some cases trigger others hence once they occur, another case must be present or must also take effect. For instance, from the log, whenever task B is being executed, task C is also executed although either of the tasks can come before or after the other. Such occurrences may occur between the cases of a driver and the truck where, for a driver to be there, there must be a truck. But it is not mandatory on who comes first because either the loading personnel could be loading or offloading the truck before the driver reports at work. When represented according to the Petri net, the log will resemble the one in figure 2. The first task and the last task are shared among the other tasks. But after the first task, the rest of the tasks run in parallel until the last task is reached. The distinction between the start and end tasks or events explicitly detects parallelism. Different tasks can be initiated at the same time and end simultaneously. But by maintaining parallelism, tasks are easily monitored ensuring easy monitoring and tasks do not mix up.
Tools Used in Process Mining
Process mining is made possible using various support tools that are available on different websites as open source materials or commercial materials. Table 2 represents some of the commercial and proven reliable tools for use in process mining. ✓ represents supported features while X represents not supported features.
Table 2: summary of the tools and their Key features
| Features | ProM | Disco | Celonis |
| Type of support | Mxml and xes | Csv, xls, mxml, xes, and fxl | Csv and xls |
| Import log size capability | No limit | Five million events | According to the database quota. |
| License | Open source | Commercial | Commercial |
| Type of output notation model | Transition systems and heuristics, petri nets, and BPMN | Fuzzy models | All Fuzzy model and other supported charts |
| Other supported platforms | Stand alone. | Stand alone | Software as a service and on premise support. |
| Data filtering | ✓ | ✓ | ✓ |
| Discriminative rule mining | ✓ | X | X |
| Social network mining | ✓ | X | X |
| Delta analysis | ✓ | ✓ | ✓ |
| Process discovery | ✓ | ✓ | ✓ |
| Performance reporting | ✓ | ✓ | ✓ |
| Conformance checking | ✓ | X | X |
| Decision rule mining | ✓ | X | X |
| Trace clustering | ✓ | X | X |
| Process visualization | ✓ | ✓ | ✓ |
As indicated in table 2, Celonis is the best tool to use when implementing the process mining in the case of We-Deliver. Celonis does similar functions as Disco although before data analysis is done it converts event logs into database elements. As opposed to the other two, it has a time stamp that has full details of the tasks timespan and not just the start and end. Data is backed up on a cloud and can be accessed from any location. This implies that all offices will be connected to one system and database through the cloud.
Conclusion
Process mining is emerging as the best solution of business intelligence that can be used to manage business process in the current contemporary business environments. As companies grow, they are faced with a challenge of ensuring there are no bottleneck processes in their operations. Process mining discovers a task, compares it to the pre-defined task through conformance, and enhances the task to create an event that is stored as a log in the database. This enables in the monitoring of tasks ensuring that there are collusions or missing forms of data and domains. There are various tools used to implement process mining in a company. For a transport logistic company operating in multiple countries, using Celonis can be effective due to its onsite database that has cloud base computing. Although an evaluation and commercial tool, Celonis can be accessed by all branches of the company through the cloud computing technology.
References
Ailenei, I.M. (2011). Process mining tools a comparative analysis. Eindhoven University of Technology. Retrieved from https://pure.tue.nl/ws/files/47023004/717803-1.pdf
Van der Aalst, W. & Weijters, A. (n.d.). process mining: a research agenda. Retrieved from http://www.processmining.org/_media/publications/aalst2004b.pdf

